网络的权重和偏置如下(这些值是随机初始化的,实际情况中会使用随机初始化):
反向传播算法利用链式法则,通过从输出层向输入层逐层计算误差梯度,高效求解神经网络参数的偏导数,以实现网络参数的优化和损失函数的最小化。
A backport is mostly used to handle stability flaws in legacy computer software or more mature variations in the software program that are still supported through the developer.
Backporting is a multi-stage approach. In this article we define The fundamental steps to produce and deploy a backport:
As discussed inside our Python web site submit, each backport can develop many undesired side effects in the IT environment.
In case you have an interest in Discovering more details on our subscription pricing options for free of charge classes, make sure you Make contact with us now.
Establish what patches, updates or modifications can be found to deal with this issue in afterwards variations of the exact same software back pr package.
的基础了,但是很多人在学的时候总是会遇到一些问题,或者看到大篇的公式觉得好像很难就退缩了,其实不难,就是一个链式求导法则反复用。如果不想看公式,可以直接把数值带进去,实际的计算一
Backporting can be a capture-all expression for almost any action that applies updates or patches from a more moderen Model of software program to an more mature Edition.
Backporting has lots of benefits, while it really is certainly not a simple correct to advanced security issues. Even more, relying on a backport during the long-phrase may introduce other protection threats, the potential risk of which can outweigh that of the initial challenge.
偏导数是指在多元函数中,对其中一个变量求导,而将其余变量视为常数的导数。
We do provide an option to pause your account for just a decreased fee, you should Get hold of our account workforce For additional particulars.
链式法则是微积分中的一个基本定理,用于计算复合函数的导数。如果一个函数是由多个函数复合而成,那么该复合函数的导数可以通过各个简单函数导数的乘积来计算。
Kamil has twenty five+ a long time of expertise in cybersecurity, specifically in community protection, Sophisticated cyber threat security, security functions and threat intelligence. Possessing been in various product management and marketing and advertising positions at businesses like Juniper, Cisco, Palo Alto Networks, Zscaler and various reducing-edge startups, he brings a singular point of view to how corporations can substantially reduce their cyber challenges with CrowdStrike's Falcon Exposure Administration.
 Angus T. Jones Then & Now!
Angus T. Jones Then & Now! Ariana Richards Then & Now!
Ariana Richards Then & Now! Sydney Simpson Then & Now!
Sydney Simpson Then & Now!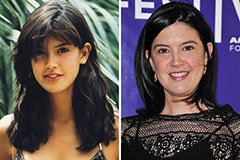 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Robbie Rist Then & Now!
Robbie Rist Then & Now!